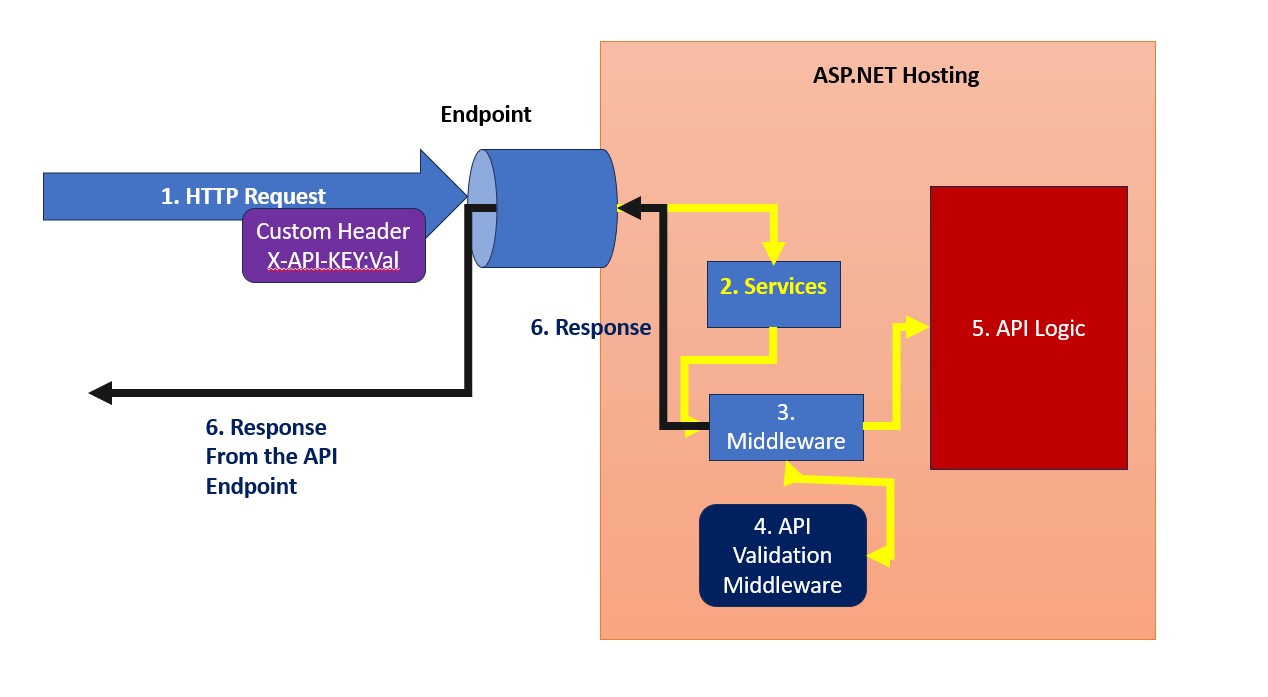
API key authentication provides a straightforward yet effective approach for securing ASP.NET Core APIs, particularly in server-to-server communication scenarios. By requiring clients to provide a valid API key with each request, this authentication mechanism offers basic security without the complexity of user-specific authorization flows. The key can be transmitted via request headers, query parameters, or request body, with header-based implementation being the most common practice. ASP.NET Core supports multiple implementation patterns including custom attributes, middleware components, endpoint filters, and policy-based authorization - each suited for different project requirements and complexity levels.
API Key Authentication Implementation Patterns
Custom Attribute with Service Filter
The service filter approach provides a flexible way to implement API key authentication through attributes. By implementing an ApiKeyAttribute that inherits from ServiceFilterAttribute, developers can create reusable authentication logic that supports dependency injection. The key components include:
csharp public class ApiKeyAttribute : ServiceFilterAttribute { public ApiKeyAttribute() : base(typeof(ApiKeyAuthorizationFilter)) { } }
This pattern, as detailed in this guide, allows for clean separation of authentication logic while maintaining flexibility through dependency injection.
API Key Storage and Validation Strategies
When implementing API key validation, several storage approaches can be used depending on security requirements:
- Database storage: Keys stored in a dedicated table with associated metadata
- Configuration files: Keys defined in appsettings.json for simple scenarios
- Key rotation: Implementing expiry and refresh mechanisms
As outlined in this resource, validation can be implemented through:
csharp public interface IApiKeyValidator { bool IsValid(string apiKey); }
The validator can check against stored keys and implement additional validation logic like:
- Key format validation
- Rate limiting checks
- Access scope verification
- Expiration validation
This approach provides flexibility while maintaining security through proper key management practices.
Introduction to API Key Authentication in .NET
Core Concepts and Purpose
API key authentication provides a straightforward security mechanism for protecting API endpoints. As outlined in this resource, this authentication method requires clients to include a valid API key with each request. The key aspects include:
- Simplicity in implementation and maintenance
- Suitable for server-to-server (S2S) communication
- Ideal for private/internal APIs with limited clients
- No complex user authentication flows required
Transport Methods and Security Considerations
According to this implementation guide, API keys can be transmitted through:
Request headers (recommended)
- Using custom headers like X-API-Key
- Provides better security than query parameters
- Helps prevent key exposure in logs
Query parameters or request body (not recommended for production)
- Higher risk of exposure through logs
- Keys visible in browser history
- Suitable only for development/testing
The transport method choice significantly impacts security - headers offer better protection by keeping keys out of URLs and logs. Additionally, proper key management practices like regular rotation and secure storage are essential for maintaining API security.
While the previous subtopic report covered implementation patterns and storage strategies, this section focuses on fundamental concepts and secure transmission methods that form the foundation for implementing API key authentication in .NET applications.
Implementation Approaches and Best Practices
Configuration and Service Registration
While previous sections covered implementation patterns, proper configuration setup is crucial for API key authentication. As detailed in this guide, the key components include:
Registering required services in Program.cs: csharp builder.Services.AddSingleton
(); builder.Services.AddSingleton<IApiKeyValidator, ApiKeyValidator>(); Configuring authorization policies: csharp services.AddAuthorization(options => { options.AddPolicy("ApiKeyPolicy", policy => policy.RequireAssertion(context => { // API key validation logic }));
});
Error Handling and Response Management
Building on the transport methods covered previously, proper error handling is essential for secure API key implementation. According to this resource, key considerations include:
Returning appropriate status codes:
- 401 Unauthorized for missing/invalid keys
- 403 Forbidden for insufficient permissions
Implementing custom error responses:
- Avoiding exposure of sensitive information
- Providing clear error messages for debugging
- Including correlation IDs for request tracing
Handling authentication failures gracefully:
- Logging failed attempts
- Rate limiting repeated failures
- Implementing retry policies where appropriate
These practices ensure robust security while maintaining good API usability and troubleshooting capabilities.
API Key Generation and Distribution
Key Generation Mechanisms
While previous sections focused on implementation and validation, secure key generation is crucial. According to this discussion, recommended approaches include:
- Using cryptographically secure random generators
- Implementing standard key formats and lengths
- Adding metadata like version and scope identifiers
- Supporting key rotation through generation timestamps
Access Control and Distribution
Building on the authentication patterns covered earlier, proper access control requires structured key distribution. Key considerations include:
Implementing key provisioning workflows:
- Automated generation via admin interfaces
- Self-service portals for approved clients
- Manual distribution for high-security scenarios
Maintaining key metadata:
- Client identification and contact details
- Usage scope and limitations
- Creation and expiry dates
- Activity monitoring data
The approach should balance security with operational needs:
- Rate limiting based on key usage
- Access restrictions by IP or other parameters
- Audit logging of key operations
- Automated key expiration handling
This focus on generation and distribution complements the implementation patterns and transport methods covered in previous sections while ensuring secure key lifecycle management.
Conclusion
API key authentication in .NET provides a robust and flexible security mechanism for protecting API endpoints, particularly suited for server-to-server communication and internal APIs. The research highlights several key implementation patterns, including custom attributes with service filters, secure storage strategies, and proper transport methods using request headers. The findings emphasize the importance of proper key generation using cryptographically secure methods, structured distribution workflows, and comprehensive validation logic including rate limiting and scope verification.
The implications suggest that while API key authentication offers simplicity and ease of implementation, it requires careful consideration of security practices throughout the key lifecycle. Organizations implementing this authentication method should focus on secure key storage, regular rotation policies, proper error handling, and comprehensive logging. Next steps should include establishing clear key management procedures, implementing monitoring systems for key usage, and ensuring proper documentation for both administrators and API consumers.